Configuring PowerShell Secure Remoting
These are the steps to configure a Windows Server to allow Pliant to connect via PowerShell Remoting over HTTPS
The following commands should be run inside a PowerShell session started with Administrator credentials
1. Enable PowerShell Remoting
Enable-PSRemoting
2. Create a self-signed HTTPS certificate to secure the encrypted connection
$CertThumb = $(New-SelfSignedCertificate -DnsName $env:COMPUTERNAME -CertStoreLocation Cert:\LocalMachine\My).Thumbprint
3. Enable HTTPS for the WinRM listener using the certificate we just created
"winrm create winrm/config/Listener?Address=*+Transport=HTTPS @{Hostname=`"${env:COMPUTERNAME}`"; CertificateThumbprint=`"$CertThumb`"}" | cmd
4. Permit PowerShell over HTTPS on the Windows Firewall
New-NetFirewallRule -DisplayName "Allow inbound PowerShell SSL TCP 5986" -Direction inbound -LocalPort 5986 -Protocol TCP -Action Allow
Pliant will use the NTLM / Negotiate authentication mechanism for WinRM connections over HTTPS
Allowing non-admin users to connect over PowerShell remoting
By default, users that are not Administrators or Domain Admins cannot connect over remote PowerShell sessions. The PowerShell block will fail with an “Access is denied.” message even though all authKey components are correct.
Add the non-admin user to the “Remote Management Users” builtin group
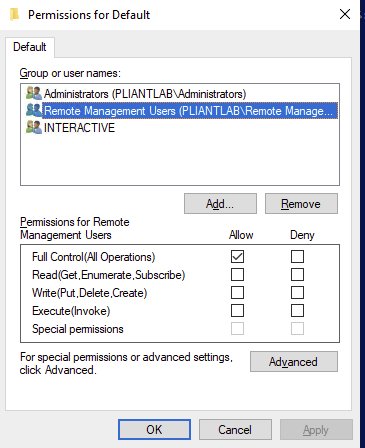
Add the “Remote Management Users” group to the default SDDL
Run this command from an Administrator PowerShell prompt:
winrm configSDDL default
Add the “Remote Management Users” group and give it Full Control permission
Add the “Remote Management Users” group to the root of the WMI control tree
Run the “Computer Management” control panel
Go to Services and Applications
Right click on WMI Control and choose Properties
Go to the Security Tab
Click on Root and then click on the Security button
Add the “Remote Management Users” group, then add “Execute Methods” and “Remote Enable” permissions for it
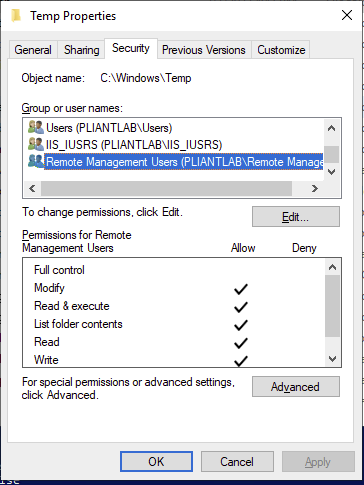
Give the “Remote Management Users” group the following file system permissions to the C:\Windows\TEMP directory