Authentication for Kubernetes
In this document, we will create an authKey that will give Pliant cluster-admin access on a Kubernetes cluster.
Prerequisites:
The cluster API must be reachable from the Pliant instance over the network
You must have access to the cluster via the kubectl utility as a cluster-admin
Note: Instructions updated for Kubernetes version 1.24 and later. Earlier K8s versions have a different behavior
Kubernetes Cluster with Internet Access
Find your Kubernetes API host
CONTEXT=$(kubectl config current-context) CLUSTER=$(kubectl config view -o json | jq -r --arg context "${CONTEXT}" '.contexts[] | select(.name == $context) | .context.cluster') kubectl config view -o json | jq -r --arg cluster "${CLUSTER}" '.clusters[] | select(.name == $cluster) | .cluster.server'| cut -d'/' -f3Run this command to create a new ServiceAccount, ClusterRoleBinding, and Secret on your Kubernetes cluster
kubectl apply -f https://distributor.pliant.io/pliant-control.yaml
Get the token for the new cluster-admin user. This token will give full cluster admin privileges to the bearer.
echo $(kubectl -n kube-system get secrets -o jsonpath="{.items[?(@.metadata.annotations['kubernetes\.io/service-account\.name']=='pliant-control')].data.token}"|awk '{print $1}'|base64 --decode)Copy out the decoded token
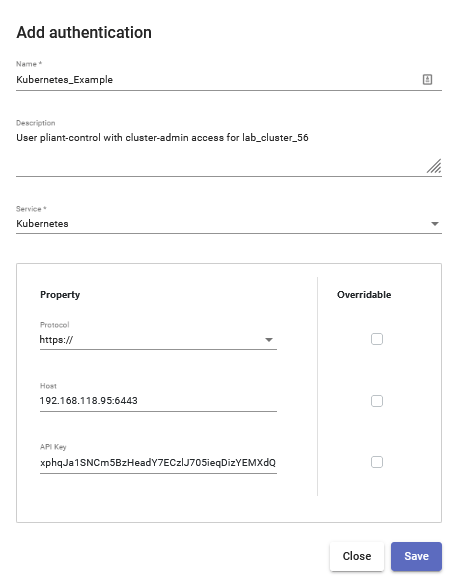
Create a new authKey for the Kubernetes service. Be sure to include the TCP port for the API if it is not using the default (443) Use the token value as the API Key.
Kubernetes Cluster without Internet Access
On your host with kubectl access, create a new file called “pliant-control.yaml” with a text editor
Paste in the following content and save the file:
apiVersion: v1 kind: ServiceAccount metadata: name: pliant-control namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: pliant-control roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: pliant-control namespace: kube-system --- apiVersion: v1 kind: Secret metadata: name: pliant-control annotations: kubernetes.io/service-account.name: "pliant-control" namespace: kube-system type: kubernetes.io/service-account-token
3. Use this command to apply the yaml and create the user:
kubectl apply -f pliant-control.yaml
4. Find your Kubernetes API host
CONTEXT=$(kubectl config current-context)
CLUSTER=$(kubectl config view -o json | jq -r --arg context "${CONTEXT}" '.contexts[] | select(.name == $context) | .context.cluster')
kubectl config view -o json | jq -r --arg cluster "${CLUSTER}" '.clusters[] | select(.name == $cluster) | .cluster.server'| cut -d'/' -f3
Now we can get the token for the new cluster-admin user. This token will give full cluster admin privileges to the bearer.
echo $(kubectl -n kube-system get secrets -o jsonpath="{.items[?(@.metadata.annotations['kubernetes\.io/service-account\.name']=='pliant-control')].data.token}"|base64 --decode)
6. Copy out the decoded token
7. Create a new authKey for the Kubernetes service. Be sure to include the TCP port for the API if it is not using the default (443) Use the token value as the API Key.